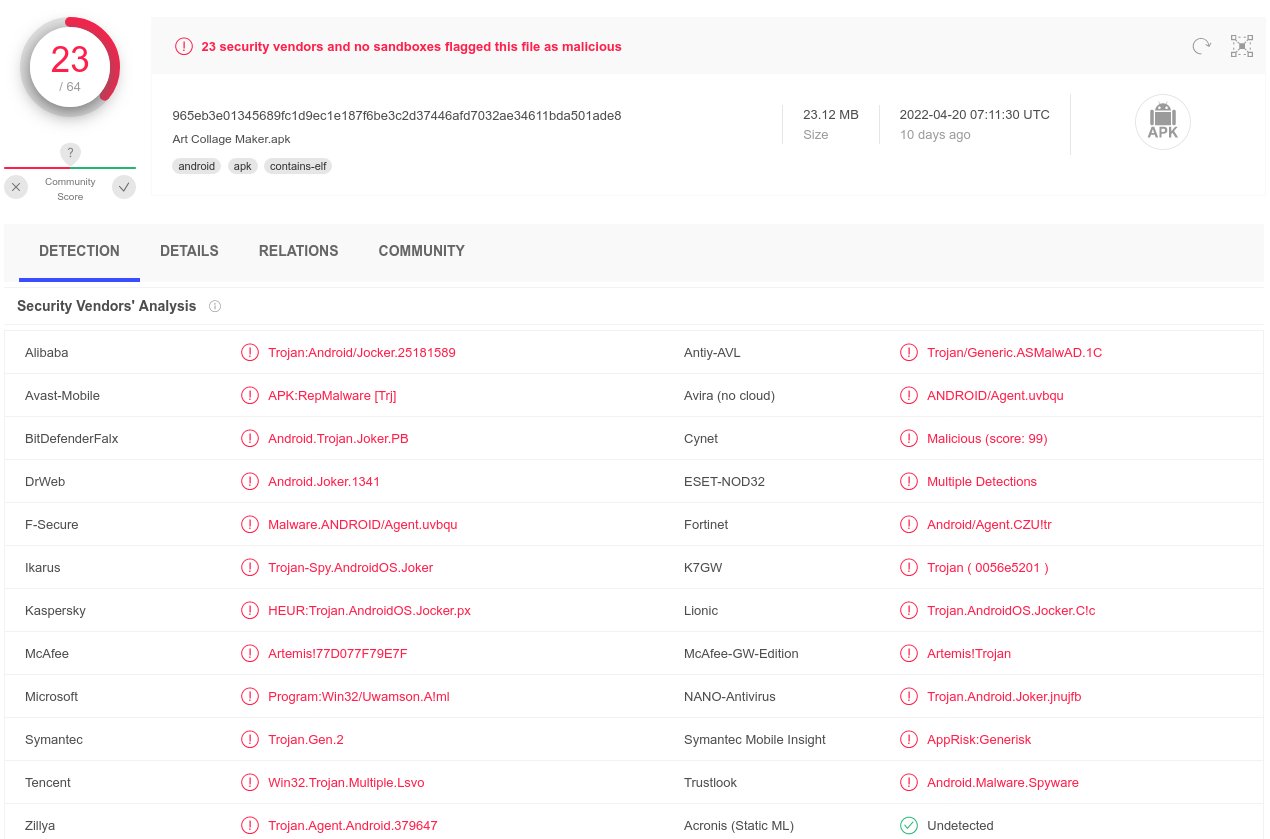
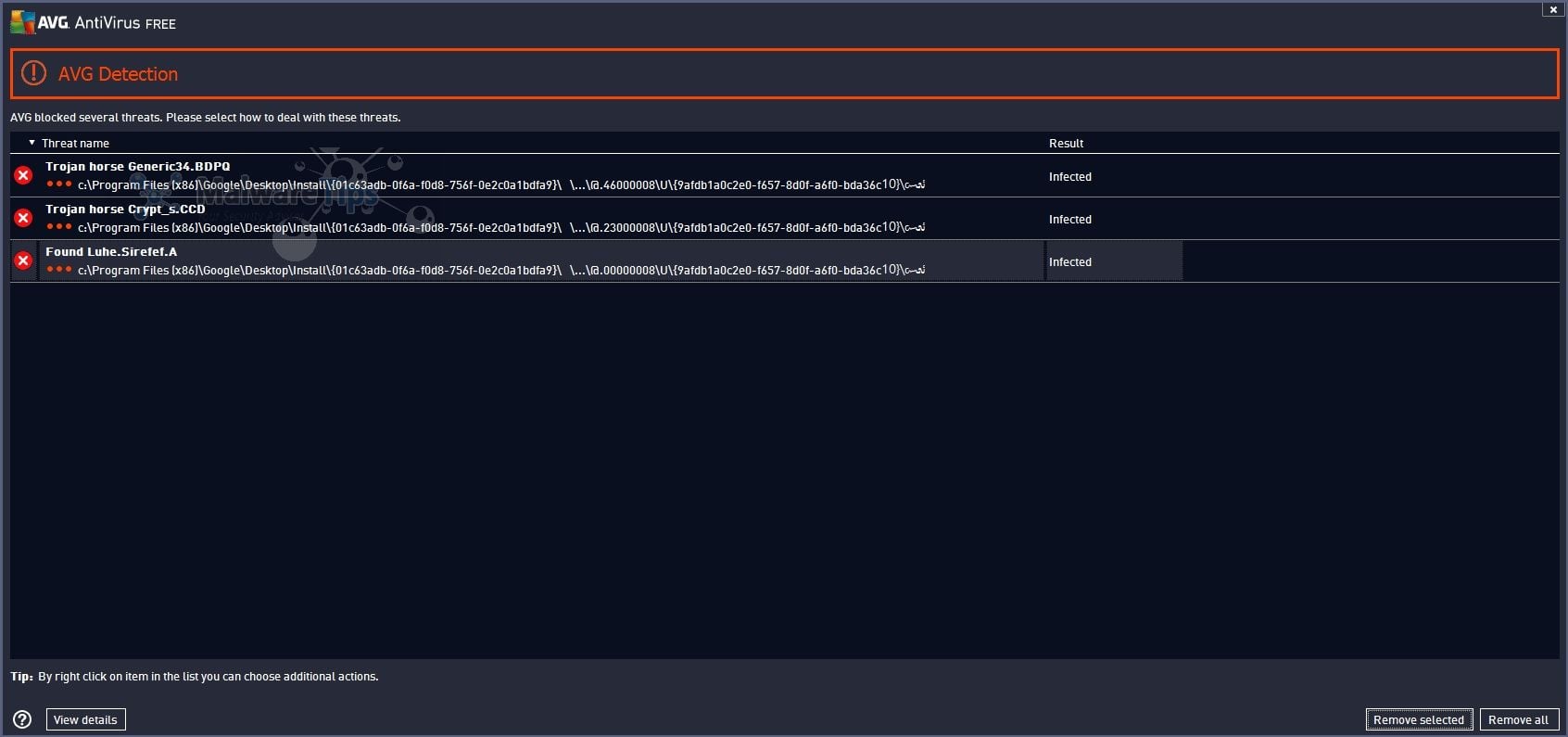
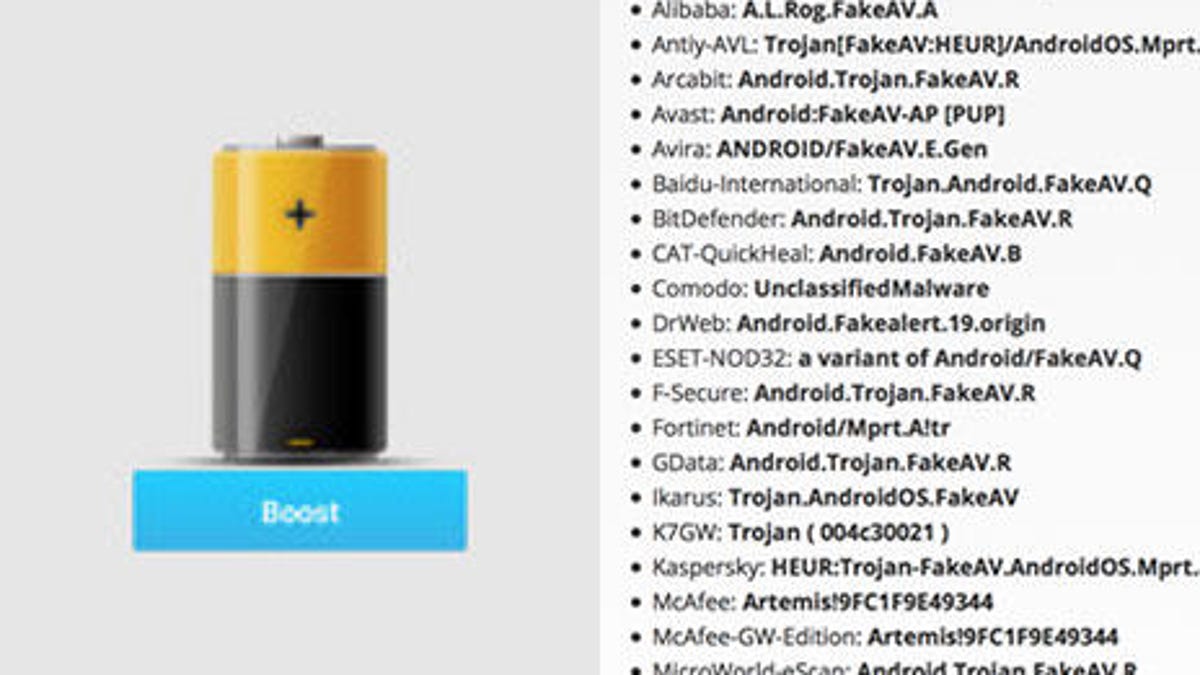
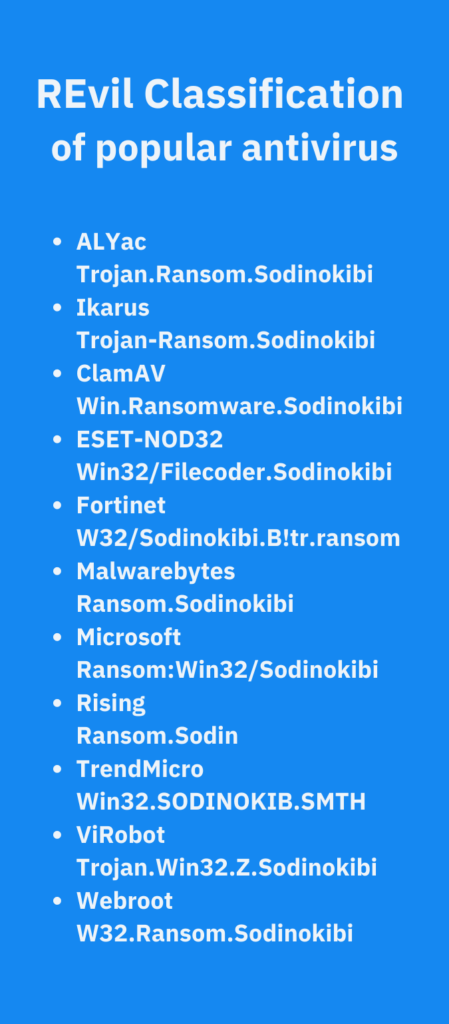
PDF] Analysing web-based malware behaviour through client honeypots
Por um escritor misterioso
Descrição
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/18-Figure1-1-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://miro.medium.com/v2/resize:fit:1400/1*AxLEGAf6cbtxmv8tgzsanw.png)
awesome-malware-analysis. A curated list of awesome malware…, by RangedMixOne
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/135-Figure7-16-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.researchgate.net/publication/319306152/figure/tbl1/AS:742638290489344@1554070174026/Hazards-which-could-be-introduced-into-a-study-by-client-honeypots-detection-module.png)
Hazards which could be introduced into a study by client honeypot's
Analysing web-based malware behaviour through client honeypots -ORCA
![PDF] Analysing web-based malware behaviour through client honeypots](https://onlinelibrary.wiley.com/cms/asset/50062d37-aa4c-4a5b-b7a5-9f7adcd381bf/nem1923-fig-0001-m.jpg)
Novel intrusion prediction mechanism based on honeypot log similarity - Jiang - 2016 - International Journal of Network Management - Wiley Online Library
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.imperva.com/learn/wp-content/uploads/sites/13/2019/11/what-is-a-honeypot.png)
What is a Honeypot, Honeynets, Spam Traps & more
![PDF] Analysing web-based malware behaviour through client honeypots](https://i1.rgstatic.net/publication/261596580_Analyzing_and_Defending_Against_Web-Based_Malware/links/0c960534c4bdd89062000000/largepreview.png)
PDF) Analyzing and Defending Against Web-Based Malware
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/61-Figure4-1-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2022/12/20135813/BlueNoroff_used_a_tactic_called_Mark-of-the-Web_01.png)
High-profile malware and targeted attacks in Q1 2023
![PDF] Analysing web-based malware behaviour through client honeypots](https://media.springernature.com/m685/springer-static/image/art%3A10.1038%2Fs41598-023-28613-0/MediaObjects/41598_2023_28613_Fig3_HTML.png)
Containerized cloud-based honeypot deception for tracking attackers
![PDF] Analysing web-based malware behaviour through client honeypots](https://ars.els-cdn.com/content/image/1-s2.0-S1574013723000679-gr3.jpg)
Flow based containerized honeypot approach for network traffic analysis: An empirical study - ScienceDirect
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.ntt-review.jp/archive_html/201210/images/fa2_fig04.jpg)
Detection, Analysis, and Countermeasure Technologies for Cyber Attacks from Evolving Malware
![PDF] Analysing web-based malware behaviour through client honeypots](https://img.yumpu.com/6958169/1/500x640/mobile-malware-attacks-and-defensepdf-adamasai.jpg)
Mobile Malware Attacks and Defense.pdf - adamas.ai
![PDF] Analysing web-based malware behaviour through client honeypots](https://faculty.nps.edu/ncrowe/oldstudents/client_honeypot_study_v7_files/image003.png)
Paper Title (use style: paper title)
de
por adulto (o preço varia de acordo com o tamanho do grupo)